Client Authenticaiton
The IKE Protocol defines several methods that can be used to authenticate a VPN Client with a VPN Gateway. To process Peer authentication, an Identity needs to be verified and credentials need to be validated using a predefined method. The Shrew Soft VPN Client supports the use of standard Preshared Key and RSA Certificate Authentication as well as the Extended and Hybrid Authentication protocol extensions.
The use of an external LDAP account database such as Microsoft Active Directory, Novell eDirectory or OpenLDAP is recommended to support Extended or Hybrid authentication. This allows for centralized account management and group membership checks to be used to limit access to private network resources.
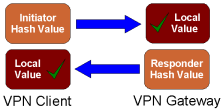
To perform Preshared Key Authentication, both Peers must have access to a common shared key value. During IKE authentication, the Peer being validated sends a Hash Value generated using the shared key and ancillary data.

The received Hash Value is then checked against a locally generated Hash Value using the same shared key and ancillary data. If the values match, the peer is considered authentic.
see also:
Configuring IPsec Tools : Preshared Key Authentication
VPN Client Configuration : Authentication Method
To perform RSA Authentication, the Peer being validated must hold a Digital Certificate signed by a trusted Certificate Authority and the Private Key for the Digital Certificate. The Peer performing the authentication only needs a copy of the trusted Certificate Authorities Digital Certificate. During IKE authentication, the Peer being validated sends a copy of the Digital Certificate and a Hash Value signed using the Private Key.
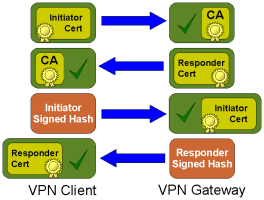
The received Digital Certificate is first verified to have been signed by the Certificate Authority Private Key. The received Hash Value is then verified to have been signed by the Digital Certificate Private Key. If both signatures are valid, the peer is considered authentic.
see also:
Configuring IPsec Tools : RSA Authentication
VPN Client Configuration : Authentication Method
To perform Extended Authentication, an ISAKMP security association will need to be established using a normal Preshared Key or RSA Authentication. Immediately after, the Client is typically required to provide a username and password. The Gateway will have access to a user account database to validate the credentials.
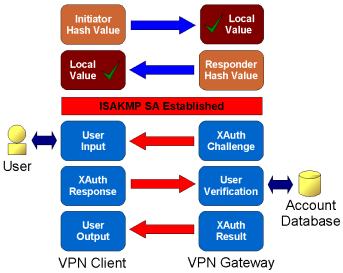
In this example, an ISAKMP security association is established using Preshared Key authentication.The security association is then used to protect the Extended Authentication which is submitted to an external account database for verification. If both the Preshared Key and Extended Authentication attempts succeed, the peer is considered authentic.
see also:
Configuring IPsec Tools : Preshared Key Authentication
Configuring IPsec Tools : User Authentication
VPN Client Configuration : Authentication Method
To perform Hybrid Authentication, an ISAKMP security association will need to be established using a modified form of RSA Authentication that only validates the Gateway. Immediately after, the Client is typically required to provide a username and password. The Gateway will have access to a user account database to validate the credentials.
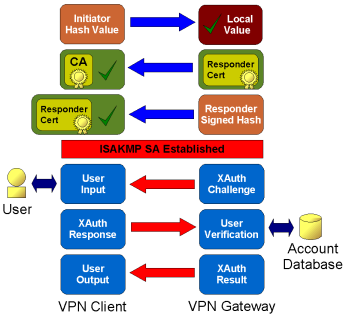
In this example, an ISAKMP security association is established using RSA authentication. The security association is then used to protect the Extended Authentication which is submitted to an external account database for verification. If both the RSA and Extended Authentication attempts succeed, the peer is considered authentic.
see also:
Configuring IPsec Tools : RSA Authentication
Configuring IPsec Tools : User Authentication
VPN Client Configuration : Authentication Method
Copyright © 2010, Shrew Soft Inc