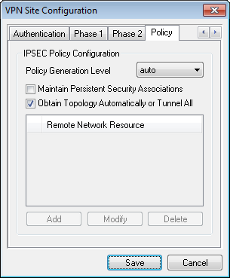
Policy Settings

Policy Generation Level
The Policy Generation Level option modifies the level in which IPsec Policies are generated. The different levels provided map to IPsec SA negotiation behaviors implemented by different vendor implementations.
Auto |
The client will attempt to automatically determine the appropriate IPsec Policy level. If the gateway offers a Cisco compatible vendor ID during phase1 negotiation, the client will select the shared level. If the gateway does not offer a Cisco compatible vendor ID, the client will select unique. |
Require |
The client will not negotiate a unique SA for each policy. Policies are generated using the local public address as the local policy ID and the Remote Network Resource as the remote policy ID. The phase2 proposal will use the policy IDs during negotiation. |
Unique |
The client will negotiate a unique SA for each policy. Policies are generated using the local public address as the local policy ID and the Remote Network Resource as the remote policy ID. The phase2 proposal will use the policy IDs during negotiation. |
Shared |
Policies are generated at the require level. However, the phase2 proposal will use the local policy ID as the local ID and Any ( 0.0.0.0/0 ) as the remote ID during negotiation. |
PLEASE NOTE: The shared level is a custom option that doesn't match standard IPsec negotiation levels. It is intended to mimic the Cisco VPN client behavior. If your gateway offers a Cisco compatible vendor ID but is not an actual Cisco VPN gateway ( ipsec-tools, NetGear and other gateways do this ), you may need to manually select the require or unique level instead of auto.
Persistent Security Associations
The Maintain Persistent Security Associations option modifies the way in which IPsec SAs are negotiated with the peer. When disabled, the client only negotiates security associations when it needs to process a packet that matches a security policy. When enabled, the client will negotiate an SA for each policy configured immediately after it connects. It then attempts to immediately renegotiate replacement security associations as they expire.
PLEASE NOTE: Maintain Persistent Security Associations option considered experimental.
IPsec Policy Configuration
The Obtain Topology Automatically or Tunnel All options modifies the way security policies are configured for the connection. When disabled, Manual configuration must be performed. When enabled, Automatic configuration is performed.
When a remote gateway is configured to support the Configuration Exchange, it provides a list of networks that are accessible via VPN Client Gateway. This network topology information, along with the client address are used to describe the security policies for this site configuration. When Automatic Policy Configuration is enabled but the remote Gateway does not supply topology information, the VPN Client will install a default policy that tunnels all traffic to the Gateway. The default value for this setting is Enabled.
The Network Topology List can be manually defined if the VPN Gateway does not provide a list automatically for the client. You can Add, Modify or Delete Network Topology List entries by using the buttons shown at the bottom of the Policy Configuration dialog. These buttons will be grayed out if the Automatic Policy Configuration option is Enabled.
The Topology Entry Dialog is used whenever you are adding or modifying a Network Topology List entry. Simply configure the Entry Type as either Include or Exclude and enter the required information. When you are finished editing the Topology Entry, press the OK button to accept the entry data or the Cancel button to discard it.
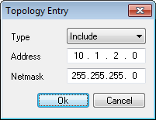
Entry Type
The Entry Type describes how the specified network should be accessed when the Client is connected to the VPN Gateway.
There are two options available:
Include |
Defines a network that should be accessed via the VPN Gateway. |
Exclude |
Defines a network that should be accessed via local connectivity. |
Address and Netmask
The Address and Netmask are used to define the Network address and size of the network.
Copyright © 2010, Shrew Soft Inc