Difference between revisions of "Howto Linksys"
| (6 intermediate revisions by the same user not shown) | |||
| Line 17: | Line 17: | ||
Using the Linksys web UI, navigate to the VPN => Client to Gateway configuration area. | Using the Linksys web UI, navigate to the VPN => Client to Gateway configuration area. | ||
| − | [[ | + | [[File:Lynksys-img1.png]] |
==== Add new group VPN ==== | ==== Add new group VPN ==== | ||
| Line 27: | Line 27: | ||
*Enable: Is greyed out. This option will become available after these changes are "Saved".<br> | *Enable: Is greyed out. This option will become available after these changes are "Saved".<br> | ||
| − | [[ | + | [[File:Lynksys-img2.png]] |
==== Local Group Setup ==== | ==== Local Group Setup ==== | ||
| Line 35: | Line 35: | ||
*Subnet mask should autopopulate with the mask of the LAN.<br> | *Subnet mask should autopopulate with the mask of the LAN.<br> | ||
| − | [[ | + | [[File:Lynksys-img3.png]] |
==== Remote Client Setup ==== | ==== Remote Client Setup ==== | ||
| Line 43: | Line 43: | ||
{This value will be needed when configuring the client}<br> | {This value will be needed when configuring the client}<br> | ||
| − | [[ | + | [[File:Lynksys-img4.png]] |
==== IPSec Setup ==== | ==== IPSec Setup ==== | ||
| Line 63: | Line 63: | ||
*Preshared Key: Use up to a 30 digit character or hexadecimal string that is difficult to brute force<br><br> | *Preshared Key: Use up to a 30 digit character or hexadecimal string that is difficult to brute force<br><br> | ||
| − | [[ | + | [[File:Lynksys-img5.png]] |
Select the 'Advanced' button for further options<br><br> | Select the 'Advanced' button for further options<br><br> | ||
| Line 75: | Line 75: | ||
3. NAT Traversal<br><br> | 3. NAT Traversal<br><br> | ||
| − | [[ | + | [[File:Lynksys-img6.png]] |
== Client Configuration == | == Client Configuration == | ||
| Line 113: | Line 113: | ||
==== Local Identity sub-tab ==== | ==== Local Identity sub-tab ==== | ||
| − | Idntification Type was configured into the router, see section titled Remote Client Setup above for these values. | + | Idntification Type was configured into the router, see section titled Remote Client Setup above for these values. |
| − | Identification Type 'Fully Qualified Domain Name'<br> | + | This guide uses: |
| − | FQDN String 'shrew.net'<br><br> | + | * Identification Type 'Fully Qualified Domain Name'<br> |
| + | * FQDN String 'shrew.net'<br><br> | ||
==== Remote Identity sub-tab ==== | ==== Remote Identity sub-tab ==== | ||
| − | Idntification Type was configured into the router, see section titled Local Group Setup above. | + | Idntification Type was configured into the router, see section titled Local Group Setup above. |
| − | Identification Type 'IP Address'<br> | + | This guide uses: |
| − | Enable 'Use a discovered remote host address'<br><br> | + | * Identification Type 'IP Address'<br> |
| + | * Enable 'Use a discovered remote host address'<br><br> | ||
==== Credentials sub-tab ==== | ==== Credentials sub-tab ==== | ||
| Line 131: | Line 133: | ||
See section IPSec Setup above. The values that are set in this tab area must match those used in the router configuration.<br><br> | See section IPSec Setup above. The values that are set in this tab area must match those used in the router configuration.<br><br> | ||
| − | Exchange Type 'aggresive'<br> | + | * Exchange Type 'aggresive'<br> |
| − | DH Exchange 'group 2'<br> | + | * DH Exchange 'group 2'<br> |
| − | Cipher Algorithm 'aes'<br> | + | * Cipher Algorithm 'aes'<br> |
| − | Cipher Key Length '256' Bits<br> | + | * Cipher Key Length '256' Bits<br> |
| − | Hash Algorithm 'sha1'<br> | + | * Hash Algorithm 'sha1'<br> |
| − | Key Life Time Limit '28800' (default)<br> | + | * Key Life Time Limit '28800' (default)<br> |
| − | Key Life Data limit '0' (default)<br><br> | + | * Key Life Data limit '0' (default)<br><br> |
=== Phase 2 Tab === | === Phase 2 Tab === | ||
| Line 143: | Line 145: | ||
See section IPSec Setup above. The values that are set in this tab area must match those used in the router configuration.<br><br> | See section IPSec Setup above. The values that are set in this tab area must match those used in the router configuration.<br><br> | ||
| − | Transform Algorithm 'esp-aes'<br> | + | * Transform Algorithm 'esp-aes'<br> |
| − | Transform Key Length '256' Bits<br> | + | * Transform Key Length '256' Bits<br> |
| − | HMAC Algorithm 'sha1'<br> | + | * HMAC Algorithm 'sha1'<br> |
| − | PFS Exchange 'group 2'<br> | + | * PFS Exchange 'group 2'<br> |
| − | Compress Algorithm 'disabled'<br> | + | * Compress Algorithm 'disabled'<br> |
| − | Key Life Time limit '3600' Secs (default)<br> | + | * Key Life Time limit '3600' Secs (default)<br> |
| − | Key Life Data limit '0' Kbytes (default)<br><br> | + | * Key Life Data limit '0' Kbytes (default)<br><br> |
=== Policy Tab === | === Policy Tab === | ||
| Line 156: | Line 158: | ||
DO Not enable either of the two options under IPSec Policy Configuration, however, select the 'Add' button to include a mapping to the remote LAN. | DO Not enable either of the two options under IPSec Policy Configuration, however, select the 'Add' button to include a mapping to the remote LAN. | ||
| − | Select 'Add' | + | * Select 'Add' |
| − | In the new window Set Type 'Include' (default) | + | ** In the new window Set Type 'Include' (default) |
| − | Address of the remote LAN. (Our example remote LAN is 192.168.0.0) | + | ** Address of the remote LAN. (Our example remote LAN is 192.168.0.0) |
| − | Netmask of the remote LAN (Our example remote LAN netmask is 255.255.255.0) | + | ** Netmask of the remote LAN (Our example remote LAN netmask is 255.255.255.0) |
| − | + | * Select 'Save' | |
| − | Select 'Save' | ||
== Additional Considerations == | == Additional Considerations == | ||
| Line 167: | Line 168: | ||
If browsing directory shares is a requirement and the WINS server is running on the remote LAN and the Shrew client is configured to find WINS, then browsing should be successful using Network Neighborhood. We have found that starting the following 2 services on the XP client enable the success. | If browsing directory shares is a requirement and the WINS server is running on the remote LAN and the Shrew client is configured to find WINS, then browsing should be successful using Network Neighborhood. We have found that starting the following 2 services on the XP client enable the success. | ||
| − | Remote Procedure Call (RPC) | + | Remote Procedure Call (RPC) <br/> |
Remote Procedure Call (RPC) Locator | Remote Procedure Call (RPC) Locator | ||
Latest revision as of 05:22, 9 January 2013
Contents
Introduction
This guide provides information that can be used to configure a Linksys RV-042 or RV-082 router to support IPsec GroupVPN client connectivity. This guide will also provide configuration information when using a Windows XPSP3 client. The current Linksys firmware version at the time of this writing is Version: 1.3.98-tm We are using Shrew version 2.1.4.
Overview
The Shrew client running on Windows XP will need to know the specifics of the remote WAN/LAN since this Linksys router does not support modcfg (ike push/pull) functionality.
Gateway Configuration
This guide assumes familiarity with configuring the Linksys router using its web UI. This Linksys router allows for multiple WAN links. This guide assumes WAN1 is the preferred link to use for the remote VPN connectivity.
It is suggested to use the routers DDNS feature if the router is assigned a non-static IP address by the ISP. The Linksys will self register any IP address changes it receives by the ISP with the selected DDNS service. If the router is in the Americas, it is suggested to create a free account at DynDNS.org and set those values in the routers DDNS configuration area, Setup->More...->DDNS
Gateway Configuration - GroupVPN
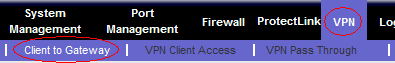
Using the Linksys web UI, navigate to the VPN => Client to Gateway configuration area.
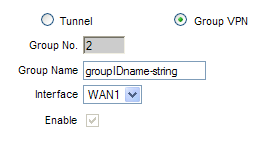
Add new group VPN
- Select the Group VPN radio button.
- Group No. is not editable and will auto increment from 1 to 2. A maximum of 2 GroupVPNs are allowable.
- Group Name: is a unique string used to identify the Group.
- Interface: Default value is WAN1. This is the interface that remote clients will connect through.
- Enable: Is greyed out. This option will become available after these changes are "Saved".
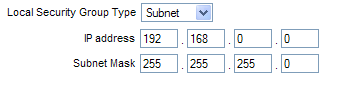
Local Group Setup
- Local Security Group Type: Choose 'subnet' from the dropdown. This will allow all systems on the LAN to access the tunnel.
- IP Address should autopopulate with the network IP block of the LAN.
- Subnet mask should autopopulate with the mask of the LAN.
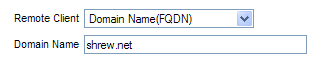
Remote Client Setup
- Remote Client: Either Domain Name(FQDN) or E-mail Address(USER FQDN) can be selected from the drop down list. We have selected Domain Name(FQDN) in this guide.
- Domain name: shrew.net
{This value will be needed when configuring the client}
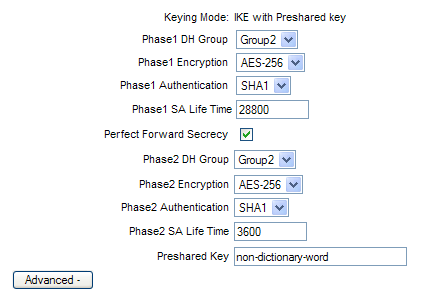
IPSec Setup
{Most of the following values will be needed when configuring the Shrew client.
- Keying Mode: IKE with Preshared key is auto selected when using GroupVPN
- Phase1 DH Group: We have selected Group 2
{Select Group 1 for network speed or Group 5 for greatest security}
- Phase1 Encryption: We have selected AES-256
{Select DES for lesser but greater speed or up to AES-256 for greatest security}
- Phase1 Authentication: We have selected SHA1
{SHA is recommended because it is more secure}
- Phase1 SA Lifetime: 28800 (default value)
- Perfect Forward Security: enable
- Phase2 DH Group: We have selected Group 2
- Phase2 Encryption: We have selected AES-256
- Phase2 Authentication: SHA1
- Phase2 SA Lifetime: 3600 (default)
- Preshared Key: Use up to a 30 digit character or hexadecimal string that is difficult to brute force
Select the 'Advanced' button for further options
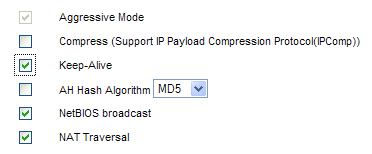
Advanced
Aggressive Mode is enabled when using GroupVPN. This cannot be changed.
Enable the following 3 advanced options leaving the rest of the options disabled.
- Keep-Alive
2. NetBIOS Broadcast (If browsing network shares is required)
3. NAT Traversal
Client Configuration
As stated earlier, the Linksys router does not support modecfg, so Shrew client will need to be configured with specific information about the connection. Also, it is suggested to run WINS from the LAN side of the Linksys if network share browsing is required.
Open the Access Manager application and create a new site configuration. Configure the settings listed below in the following tabs.
General Tab
The Remote Host section must be configured. The Host Name or IP Address is defined as either the static IP address assigned to the WAN interface of the router or it's DDNS hostname.
The Auto Configuration mode should be set to 'disabled'.
Set the Address Method to "Use a Virtual Adaptor and assigned address", then choose and address which is NOT in the current range of the Windows XP (client) network (local LAN) AND not in the current range of the LAN side of the Linksys (remote LAN). For example,
The client used in this guide is on a local LAN of 10.1.1.0 with a subnet of 255.255.255.0. The LAN side of the Linksys is on a remote LAN of 192.168.0.0 with a subnet of 255.255.255.0. For this Shrew client configuration, we will choose an address of 192.168.30.0 with a subnet of 255.255.255.0
Set MTU to '1380' (default)
Client Tab
Set NAT Traversal to 'enable'
Nat Traversal Port to '4500' (default)
Keep alive packet rate '15' secs (default)
IKE Fragmentation 'disable'
Name Resolution Tab
Enable WINS and key in the IP address of the WINS server of the remote LAN.
Enable DNS and key in the IP address of the DNS server of the remote LAN. In most cases, the IP address of the LAN interface of the router will be successful. The LAN side of the router used in this example is 192.168.0.1
Key in a domain suffix if the remote LAN is set to use such value
DO Not enable 'SPlit DNS', this is not supported by the Linksys
Authentication Tab
Set Authentication Method to 'Mutual PSK' in the drop down menu
Local Identity sub-tab
Idntification Type was configured into the router, see section titled Remote Client Setup above for these values. This guide uses:
- Identification Type 'Fully Qualified Domain Name'
- FQDN String 'shrew.net'
Remote Identity sub-tab
Idntification Type was configured into the router, see section titled Local Group Setup above. This guide uses:
- Identification Type 'IP Address'
- Enable 'Use a discovered remote host address'
Credentials sub-tab
Key in the Pre-Shared Key, a non-dictionary word that was configured into the router. See section IPSec Setup above.
Phase 1 Tab
See section IPSec Setup above. The values that are set in this tab area must match those used in the router configuration.
- Exchange Type 'aggresive'
- DH Exchange 'group 2'
- Cipher Algorithm 'aes'
- Cipher Key Length '256' Bits
- Hash Algorithm 'sha1'
- Key Life Time Limit '28800' (default)
- Key Life Data limit '0' (default)
Phase 2 Tab
See section IPSec Setup above. The values that are set in this tab area must match those used in the router configuration.
- Transform Algorithm 'esp-aes'
- Transform Key Length '256' Bits
- HMAC Algorithm 'sha1'
- PFS Exchange 'group 2'
- Compress Algorithm 'disabled'
- Key Life Time limit '3600' Secs (default)
- Key Life Data limit '0' Kbytes (default)
Policy Tab
Here we must give access to the Remote LAN network resources.[[BR] DO Not enable either of the two options under IPSec Policy Configuration, however, select the 'Add' button to include a mapping to the remote LAN.
- Select 'Add'
- In the new window Set Type 'Include' (default)
- Address of the remote LAN. (Our example remote LAN is 192.168.0.0)
- Netmask of the remote LAN (Our example remote LAN netmask is 255.255.255.0)
- Select 'Save'
Additional Considerations
If browsing directory shares is a requirement and the WINS server is running on the remote LAN and the Shrew client is configured to find WINS, then browsing should be successful using Network Neighborhood. We have found that starting the following 2 services on the XP client enable the success.
Remote Procedure Call (RPC)
Remote Procedure Call (RPC) Locator
Credits
This guide was submitted by Drew Flickema. Happy Tunneling <><
Thanks Shrew!