Difference between revisions of "Howto m0n0wall"
| (13 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
| − | + | == Introduction == | |
This guide provides information that can be used to configure m0n0wall running pb25 or later to support IPsec VPN client connectivity. The Shrew Soft VPN Client has been reported to inter-operate correctly with m0n0wall. | This guide provides information that can be used to configure m0n0wall running pb25 or later to support IPsec VPN client connectivity. The Shrew Soft VPN Client has been reported to inter-operate correctly with m0n0wall. | ||
| Line 9: | Line 9: | ||
*IP Address | *IP Address | ||
| − | + | == Gateway Configuration == | |
This example assumes you have knowledge of m0n0wall web configuration interface. For more information, please consult the [http://doc.m0n0.ch/handbook/ m0n0wall handbook]. | This example assumes you have knowledge of m0n0wall web configuration interface. For more information, please consult the [http://doc.m0n0.ch/handbook/ m0n0wall handbook]. | ||
| − | |||
| − | |||
#Log into your m0n0wall and go to the IPsec: Mobile clients page. | #Log into your m0n0wall and go to the IPsec: Mobile clients page. | ||
| − | + | #Configure the settings as shown in the following picture: | |
| − | + | [[File:monowall_1.png]]<br/> | |
| − | |||
| − | [[ | ||
| − | |||
You '''must''' use aggressive mode, as only IP addresses can be used as identifiers in main mode. | You '''must''' use aggressive mode, as only IP addresses can be used as identifiers in main mode. | ||
| + | # Click "Save", then go to the IPsec: Pre-shared keys page. | ||
| + | # Add a new key for each mobile user (use different keys, and at least 8 characters!). Use the e-mail address of the corresponding user as the identifier. | ||
| + | # Go to the IPsec: Tunnels page, check "Enable IPsec" and click "Save". | ||
| − | + | == Client Configuration == | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
The client configuration in this example is straight forward. Open the Access Manager application and create a new site configuration. Configure the settings listed below in the following tabs. | The client configuration in this example is straight forward. Open the Access Manager application and create a new site configuration. Configure the settings listed below in the following tabs. | ||
| − | + | === General Tab === | |
The Remote Host section must be configured. The ''Host Name or IP Address'' is defined to match the m0n0wall public ip address. The ''Auto Configuration'' mode should be set to ''ike config pull''. | The Remote Host section must be configured. The ''Host Name or IP Address'' is defined to match the m0n0wall public ip address. The ''Auto Configuration'' mode should be set to ''ike config pull''. | ||
| Line 39: | Line 31: | ||
The Local Host section must also be configured. The ''Address Method'' should be set to ''use an existing adapter and current address''. This will make is so that you can still see all the computers on your m0n0wall network, but you will not physically be a part of that network. | The Local Host section must also be configured. The ''Address Method'' should be set to ''use an existing adapter and current address''. This will make is so that you can still see all the computers on your m0n0wall network, but you will not physically be a part of that network. | ||
| − | + | === Client Tab === | |
The Firewall section must be configured. The ''Keep-alive packet rate'' should be set to 30. The ''IKE Fragmentation'' should be set to ''disable''. | The Firewall section must be configured. The ''Keep-alive packet rate'' should be set to 30. The ''IKE Fragmentation'' should be set to ''disable''. | ||
| Line 45: | Line 37: | ||
The Other Options must also be configured. The ''Enable Client Login Banner'' should be ''unchecked''. | The Other Options must also be configured. The ''Enable Client Login Banner'' should be ''unchecked''. | ||
| − | + | === Name Resolution Tab === | |
The WINS /DNS section must be configured. The ''Enable WINS'' and ''Enable DNS'' should be ''unchecked''. | The WINS /DNS section must be configured. The ''Enable WINS'' and ''Enable DNS'' should be ''unchecked''. | ||
| − | + | === Authentication Tab === | |
The client authentication settings must be configured. The Authentication Method is defined as ''Mututal PSK''. | The client authentication settings must be configured. The Authentication Method is defined as ''Mututal PSK''. | ||
| − | + | ==== Local Identity Sub-Tab ==== | |
The Local Identity parameters are defined as ''Identification Type'' with a ''User Fully Qulaified Domain Name'' "email address" to match the m0n0wall configuration. | The Local Identity parameters are defined as ''Identification Type'' with a ''User Fully Qulaified Domain Name'' "email address" to match the m0n0wall configuration. | ||
| − | + | ==== Remote Identity Sub-Tab ==== | |
The Remote Identity parameters are defined as ''Identification Type'' with a ''IP Address'' of ''Use a discovered remote host address''. | The Remote Identity parameters are defined as ''Identification Type'' with a ''IP Address'' of ''Use a discovered remote host address''. | ||
| − | + | ==== Credentials Sub-Tab ==== | |
The Credentials ''Pre Shared Key'' is defined as "Pre-shared key" to match the m0n0wall configuration. | The Credentials ''Pre Shared Key'' is defined as "Pre-shared key" to match the m0n0wall configuration. | ||
| − | + | === Phase 1 Tab === | |
The Proposal section must be configured. The ''Exchange Type'' is set to ''aggressive'' and the ''DH Exchange'' is set to ''group 2'' and the ''Cipher Algorithm'' is set to ''3des'' and the ''Hash Algorithm'' is set to ''sha1'' and the ''Key Life Time limit'' is set to ''54600'' to match the m0n0wall configuration. | The Proposal section must be configured. The ''Exchange Type'' is set to ''aggressive'' and the ''DH Exchange'' is set to ''group 2'' and the ''Cipher Algorithm'' is set to ''3des'' and the ''Hash Algorithm'' is set to ''sha1'' and the ''Key Life Time limit'' is set to ''54600'' to match the m0n0wall configuration. | ||
| − | + | === Phase 2 Tab === | |
The Proposal section must be configured. The ''Transform Algorithm'' is set to ''esp-3des'' and the ''HMAC Algorithm'' is set to ''sha1'' and the ''PFS Exchange'' is set to ''group 2'' and the ''Key Life Time limit'' is set to ''28800'' to match the m0n0wall configuration. | The Proposal section must be configured. The ''Transform Algorithm'' is set to ''esp-3des'' and the ''HMAC Algorithm'' is set to ''sha1'' and the ''PFS Exchange'' is set to ''group 2'' and the ''Key Life Time limit'' is set to ''28800'' to match the m0n0wall configuration. | ||
| − | + | === Policy Tab === | |
The IPsec Policy information must be manually configured when communicating with m0n0wall gateways. Be sure to ''unckeck'' both ''Maintain Persistent Secure Associations'' and ''Obtain Topology Automatically or Tunnel All''. Create an include Topology entry for each IPsec Policy network created on the gateway. For our example, a single Topology Entry is defined to include the 10.1.2.0/24 network. | The IPsec Policy information must be manually configured when communicating with m0n0wall gateways. Be sure to ''unckeck'' both ''Maintain Persistent Secure Associations'' and ''Obtain Topology Automatically or Tunnel All''. Create an include Topology entry for each IPsec Policy network created on the gateway. For our example, a single Topology Entry is defined to include the 10.1.2.0/24 network. | ||
| Line 83: | Line 75: | ||
=== Resources === | === Resources === | ||
| − | + | [[Media:M0n0wall.vpn.txt]] | |
=== Credits === | === Credits === | ||
This guide was submitted by Chris Andrist. | This guide was submitted by Chris Andrist. | ||
Latest revision as of 04:44, 9 January 2013
Introduction
This guide provides information that can be used to configure m0n0wall running pb25 or later to support IPsec VPN client connectivity. The Shrew Soft VPN Client has been reported to inter-operate correctly with m0n0wall.
Overview
The configuration example described below will allow an IPsec VPN client to communicate with a single remote private network. The client will use the pull configuration method to acquire the following parameters automatically from m0n0wall.
- IP Address
Gateway Configuration
This example assumes you have knowledge of m0n0wall web configuration interface. For more information, please consult the m0n0wall handbook.
- Log into your m0n0wall and go to the IPsec: Mobile clients page.
- Configure the settings as shown in the following picture:
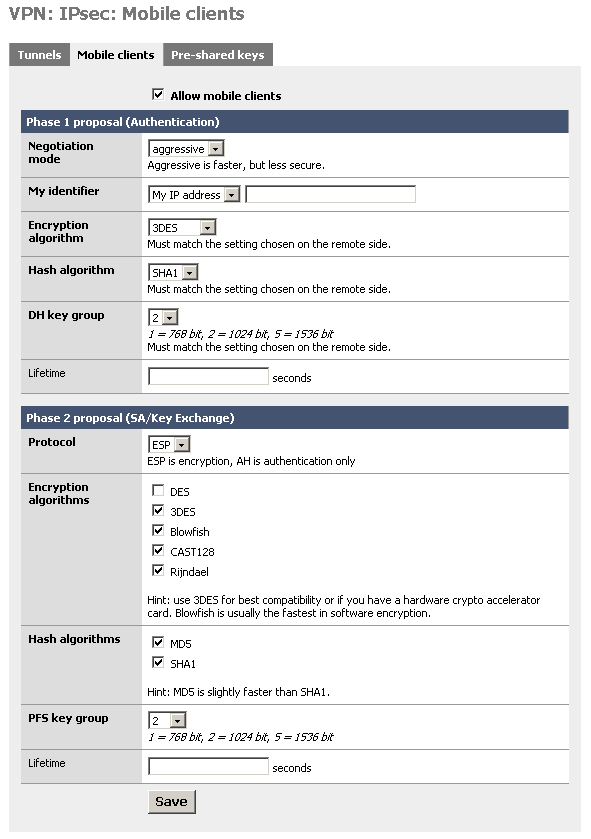
You must use aggressive mode, as only IP addresses can be used as identifiers in main mode.
- Click "Save", then go to the IPsec: Pre-shared keys page.
- Add a new key for each mobile user (use different keys, and at least 8 characters!). Use the e-mail address of the corresponding user as the identifier.
- Go to the IPsec: Tunnels page, check "Enable IPsec" and click "Save".
Client Configuration
The client configuration in this example is straight forward. Open the Access Manager application and create a new site configuration. Configure the settings listed below in the following tabs.
General Tab
The Remote Host section must be configured. The Host Name or IP Address is defined to match the m0n0wall public ip address. The Auto Configuration mode should be set to ike config pull.
The Local Host section must also be configured. The Address Method should be set to use an existing adapter and current address. This will make is so that you can still see all the computers on your m0n0wall network, but you will not physically be a part of that network.
Client Tab
The Firewall section must be configured. The Keep-alive packet rate should be set to 30. The IKE Fragmentation should be set to disable.
The Other Options must also be configured. The Enable Client Login Banner should be unchecked.
Name Resolution Tab
The WINS /DNS section must be configured. The Enable WINS and Enable DNS should be unchecked.
Authentication Tab
The client authentication settings must be configured. The Authentication Method is defined as Mututal PSK.
Local Identity Sub-Tab
The Local Identity parameters are defined as Identification Type with a User Fully Qulaified Domain Name "email address" to match the m0n0wall configuration.
Remote Identity Sub-Tab
The Remote Identity parameters are defined as Identification Type with a IP Address of Use a discovered remote host address.
Credentials Sub-Tab
The Credentials Pre Shared Key is defined as "Pre-shared key" to match the m0n0wall configuration.
Phase 1 Tab
The Proposal section must be configured. The Exchange Type is set to aggressive and the DH Exchange is set to group 2 and the Cipher Algorithm is set to 3des and the Hash Algorithm is set to sha1 and the Key Life Time limit is set to 54600 to match the m0n0wall configuration.
Phase 2 Tab
The Proposal section must be configured. The Transform Algorithm is set to esp-3des and the HMAC Algorithm is set to sha1 and the PFS Exchange is set to group 2 and the Key Life Time limit is set to 28800 to match the m0n0wall configuration.
Policy Tab
The IPsec Policy information must be manually configured when communicating with m0n0wall gateways. Be sure to unckeck both Maintain Persistent Secure Associations and Obtain Topology Automatically or Tunnel All. Create an include Topology entry for each IPsec Policy network created on the gateway. For our example, a single Topology Entry is defined to include the 10.1.2.0/24 network.
Known Issues
None reported.
Resources
Credits
This guide was submitted by Chris Andrist.